A perspective on life, from one corner of the world, on the times we find ourselves living in...
Saturday, March 15, 2014
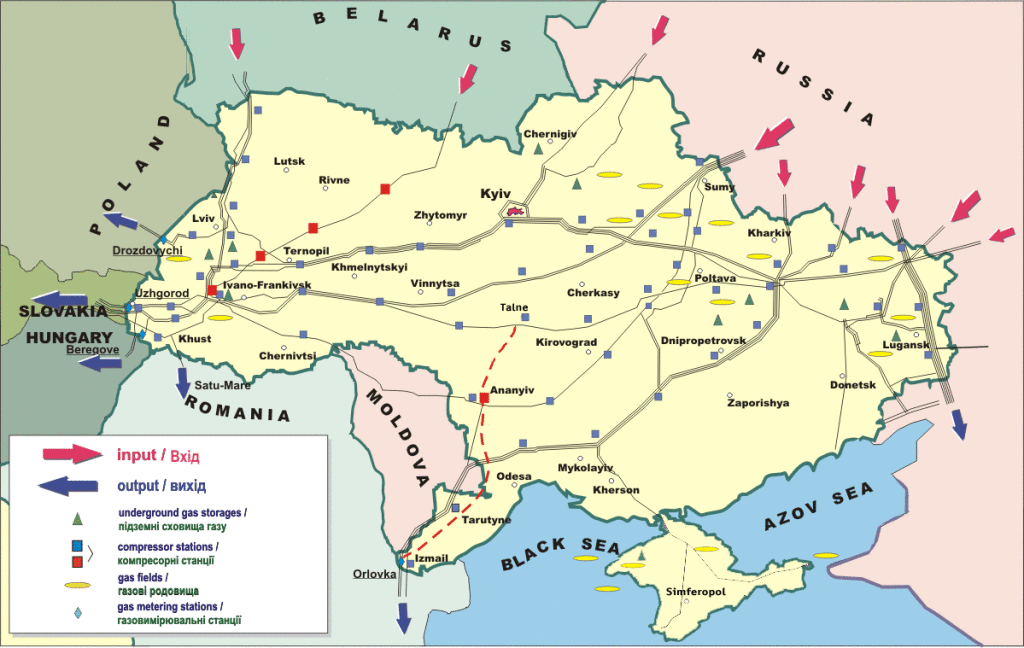
All You Need to Know About Ukraine
All You Need to Know About Ukraine
The world is SCREAMING for a new financial system
The world is SCREAMING for a new financial system
Ambergris Caye, Belize
One of the key lessons we can take away from history is that the global financial system changes… frequently.
In ancient times, Roman coins were used across the region by Romans and non-Romans alike who engaged in trade and commerce.
Given how destructively successive Roman governments debased their coins, however, the reserve burden eventually fell to the Byzantine Empire, whose gold solidus coin became the dominant currency in world trade.
Over the centuries, this standard changed several more times. The Venetians, Florentines, Spanish, French, British, etc. each issued the world’s dominant currency at one point or another.
But the fundamentals of those currencies changed. Governments engaged in wanton debasement, mismanaged their economies, and accumulated massive debt levels. And eventually the world shifted to new currencies.
Since the end of World War II, the US dollar has been the dominant currency in the world.
And even though Richard Nixon ended the dollar’s convertability to gold and unilaterally abandoned the US government’s obligations under the Bretton Woods system back in 1971, the world has still clung to the dollar for the past 43-years.
But this is changing rapidly.
The Chinese, which have their own economic issues to deal with, are starting to dump Treasuries in record numbers.
Central banks are buying up more gold. Foreign countries are entering into bilateral currency swap arrangements with one another. And world governments are starting to (rather embarrassingly) demand that the US get its budget and fiscal house in order.
Most tellingly, though, member nations of the International Monetary Fund are starting to revolt.
As one of the major organizations spawned from the post-war financial structure, the IMF’s original goal was to ensure the smooth development of a new global financial system.
Over 180 countries have since become members of the IMF. But the organization runs on a quota system, with each member nation having a certain percentage of the IMF’s overall votes.
The US, for example, has the most power by far with a 16.75% share of the vote. Japan is a distant second with a 6.23% share.
This puts the US in the driver’s seat. And it’s been that way for decades.
But most of the other 180+ nations have had enough. And they’re pushing the United States to massively overhaul the current quota system.
Even typical allies are breaking ranks. Australian Treasurer Joe Hockey recently told reporters at a financial conference that they will “actively lobby” the US to reform the IMF quota issues, and that “Congress must understand that it is in the interest of the US to reform the IMF. . .”
India. China. Just about everyone imaginable is pushing for major IMF reform. Everyone except the Land of the Free. The US government seems to like things the way they are. And Congress has been very intransigent in adopting any planned reforms.
These people have their heads buried in the sand so deep that they can’t even hear the rest of the world SCREAMING for a new financial system.
This is going to happen, whether the US wants it to or not.
And while no foreign government wants a collapse of the dollar, they do very much want an orderly rebalancing of the financial system. This is already under way.
The US government may pretend that everything is fine and dandy. But given the overwhelming objective evidence out there, folks who aren’t on board with this major trend are ignoring it at their own peril.
Thursday, March 13, 2014
The Most Evil And Disturbing NSA Spy Practices To-Date Have Just Been Revealed
The Most Evil And Disturbing NSA Spy Practices To-Date Have Just Been Revealed
Submitted by Mike Krieger of Liberty Blitzkrieg blog,
In some cases the NSA has masqueraded as a fake Facebook server, using the social media site as a launching pad to infect a target’s computer and exfiltrate files from a hard drive. In others, it has sent out spam emails laced with the malware, which can be tailored to covertly record audio from a computer’s microphone and take snapshots with its webcam. The hacking systems have also enabled the NSA to launch cyberattacks by corrupting and disrupting file downloads or denying access to websites.
The man-in-the-middle tactic can be used, for instance, to covertly change the content of a message as it is being sent between two people, without either knowing that any change has been made by a third party.
- From Glenn Greenwald’s latest article: How the NSA Plans to Infect Millions of Computers with Malware
The latest piece from Greenwald and company on the unconstitutional spy practices of the NSA may represent the most dangerous and disturbing revelations yet. It’s hard for shadiness at the NSA to surprise me these days, but there was only one word that kept repeating over and over in my head as I read this: EVIL.
As a quick aside, Greenwald points out in the quote above how spam emails are used by the NSA to bait you into clicking dangerous links. This is a timely revelation considering I received one such email yesterday from a friend of mine. The email was sent to a wide list of let’s say “liberty-minded people” and webmasters associated with very popular sites. The link seemed shady so I texted him to ask if he had sent it. He hadn’t.
Earlier this week, during a talk at SXSW, Edward Snowden pleaded with people to use encryption. While he admitted if the NSA targeted you individually they could almost certainly “own your computer,” he stated that if people use encryption on a massive scale it makes the NSA’s attempts to monitor everyone at the same time much more difficult.
As Mikko Hypponen, an expert in malware stated:
Move along serfs, nothing to see here.“The NSA’s surveillance techniques could inadvertently be undermining the security of the Internet.”
From The Intercept:
Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process.
The classified files – provided previously by NSA whistleblower Edward Snowden – contain new details about groundbreaking surveillance technology the agency has developed to infect potentially millions of computers worldwide with malware “implants.” The clandestine initiative enables the NSA to break into targeted computers and to siphon out data from foreign Internet and phone networks.
In some cases the NSA has masqueraded as a fake Facebook server, using the social media site as a launching pad to infect a target’s computer and exfiltrate files from a hard drive. In others, it has sent out spam emails laced with the malware, which can be tailored to covertly record audio from a computer’s microphone and take snapshots with its webcam. The hacking systems have also enabled the NSA to launch cyberattacks by corrupting and disrupting file downloads or denying access to websites.
The implants being deployed were once reserved for a few hundred hard-to-reach targets, whose communications could not be monitored through traditional wiretaps. But the documents analyzed by The Intercept show how the NSA has aggressively accelerated its hacking initiatives in the past decade by computerizing some processes previously handled by humans. The automated system – codenamed TURBINE – is designed to “allow the current implant network to scale to large size (millions of implants) by creating a system that does automated control implants by groups instead of individually.”
Mikko Hypponen, an expert in malware who serves as chief research officer at the Finnish security firm F-Secure, calls the revelations “disturbing.” The NSA’s surveillance techniques, he warns, could inadvertently be undermining the security of the Internet.
It sounds like that is precisely their intent…
The NSA began rapidly escalating its hacking efforts a decade ago. In 2004, according to securet internal records, the agency was managing a small network of only 100 to 150 implants. But over the next six to eight years, as an elite unit called Tailored Access Operations (TAO) recruited new hackers and developed new malware tools, the number of implants soared to tens of thousands.
The agency’s solution was TURBINE. Developed as part of TAO unit, it is described in the leaked documents as an “intelligent command and control capability” that enables “industrial-scale exploitation.”
Earlier reports based on the Snowden files indicate that the NSA has already deployed between 85,000 and 100,000 of its implants against computers and networks across the world, with plans to keep on scaling up those numbers.
The intelligence community’s top-secret “Black Budget” for 2013, obtained by Snowden, lists TURBINE as part of a broader NSA surveillance initiative named “Owning the Net.”
The agency sought $67.6 million in taxpayer funding for its Owning the Net program last year. Some of the money was earmarked for TURBINE, expanding the system to encompass “a wider variety” of networks and “enabling greater automation of computer network exploitation.”
Your tax dollars at works slaves.
One implant, codenamed UNITEDRAKE, can be used with a variety of “plug-ins” that enable the agency to gain total control of an infected computer.
An implant plug-in named CAPTIVATEDAUDIENCE, for example, is used to take over a targeted computer’s microphone and record conversations taking place near the device. Another, GUMFISH, can covertly take over a computer’s webcam and snap photographs. FOGGYBOTTOM records logs of Internet browsing histories and collects login details and passwords used to access websites and email accounts. GROK is used to log keystrokes. And SALVAGERABBIT exfiltrates data from removable flash drives that connect to an infected computer.
The implants can enable the NSA to circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks. That’s because the NSA’s malware gives the agency unfettered access to a target’s computer before the user protects their communications with encryption.
According to the Snowden files, the technology has been used to seek out terror suspects as well as individuals regarded by the NSA as “extremist.” But the mandate of the NSA’s hackers is not limited to invading the systems of those who pose a threat to national security.
In one secret post on an internal message board, an operative from the NSA’s Signals Intelligence Directorate describes using malware attacks against systems administrators who work at foreign phone and Internet service providers. By hacking an administrator’s computer, the agency can gain covert access to communications that are processed by his company. “Sys admins are a means to an end,” the NSA operative writes.But not all of the NSA’s implants are used to gather intelligence, the secret files show. Sometimes, the agency’s aim is disruption rather than surveillance. QUANTUMSKY, a piece of NSA malware developed in 2004, is used to block targets from accessing certain websites.
QUANTUMCOPPER, first tested in 2008, corrupts a target’s file downloads. These two “attack” techniques are revealed on a classified list that features nine NSA hacking tools, six of which are used for intelligence gathering. Just one is used for “defensive” purposes – to protect U.S. government networks against intrusions.
Before it can extract data from an implant or use it to attack a system, the NSA must first install the malware on a targeted computer or network.
According to one top-secret document from 2012, the agency can deploy malware by sending out spam emails that trick targets into clicking a malicious link. Once activated, a “back-door implant” infects their computers within eight seconds.
Consequently, the NSA has turned to new and more advanced hacking techniques. These include performing so-called “man-in-the-middle” and “man-on-the-side” attacks, which covertly force a user’s internet browser to route to NSA computer servers that try to infect them with an implant.
In one man-on-the-side technique, codenamed QUANTUMHAND, the agency disguises itself as a fake Facebook server. When a target attempts to log in to the social media site, the NSA transmits malicious data packets that trick the target’s computer into thinking they are being sent from the real Facebook. By concealing its malware within what looks like an ordinary Facebook page, the NSA is able to hack into the targeted computer and covertly siphon out data from its hard drive. A top-secret animation demonstrates the tactic in action.
The man-in-the-middle tactic can be used, for instance, to covertly change the content of a message as it is being sent between two people, without either knowing that any change has been made by a third party. The same technique is sometimes used by criminal hackers to defraud people.
“The thing that raises a red flag for me is the reference to ‘network choke points,’” he says. “That’s the last place that we should be allowing intelligence agencies to compromise the infrastructure – because that is by definition a mass surveillance technique.”
In many cases, firewalls and other security measures do not appear to pose much of an obstacle to the NSA. Indeed, the agency’s hackers appear confident in their ability to circumvent any security mechanism that stands between them and compromising a computer or network. “If we can get the target to visit us in some sort of web browser, we can probably own them,” an agency hacker boasts in one secret document. “The only limitation is the ‘how.’”
When even the GCHQ is questioning the legality of a surveillance program you know you’ve gone too far. Way too far.
GCHQ cooperated with the hacking attacks despite having reservations about their legality. One of the Snowden files, previously disclosed by Swedish broadcaster SVT, revealed that as recently as April 2013, GCHQ was apparently reluctant to get involved in deploying the QUANTUM malware due to “legal/policy restrictions.” A representative from a unit of the British surveillance agency, meeting with an obscure telecommunications standards committee in 2010, separately voiced concerns that performing “active” hacking attacks for surveillance “may be illegal” under British law.
Full article here
Wednesday, March 12, 2014
Proved Reserves Of Oil, Gas, And Coal By Country
Click Here: Proved Reserves Of Oil, Gas, And Coal By Country
Proved Reserves of Fossil Fuels
Proved Reserves of Oil, Gas, and Coal by Country 2010
This data set shows the proved reserves of oil, gas and coal, by country in 2010. Values for gas and coal were standardized to million tonnes of oil equivalent (mtoe).
Source: BP Statistical Review of World Energy. June 2011.
Link: click here for more information
This data set shows the proved reserves of oil, gas and coal, by country in 2010. Values for gas and coal were standardized to million tonnes of oil equivalent (mtoe).
Source: BP Statistical Review of World Energy. June 2011.
Link: click here for more information
Subscribe to:
Comments (Atom)
Interesting Sites to Checkout
-
-
Pork Bellies are Gone, But Stores Still Have Bacon - Great and Wonderful Tuesday Morning Folks, The tamp continues, sort of, with Gold now up 20 cents at $1,675.40 after dipping to $1,667.50 with the hig...3 years ago
-
More Fed Meetings; Gold and Silver Remain “Cheap” | CAMI - Please click below: More Fed Meetings; Gold and Silver Remain “Cheap” | CAMI13 years ago
-
-
-
-
Blog Archive
- 09/10 - 09/17 (1)
- 08/20 - 08/27 (1)
- 07/02 - 07/09 (3)
- 06/25 - 07/02 (22)
- 06/18 - 06/25 (20)
- 06/11 - 06/18 (35)
- 06/04 - 06/11 (16)
- 05/21 - 05/28 (4)
- 05/14 - 05/21 (4)
- 10/30 - 11/06 (3)
- 03/22 - 03/29 (1)
- 02/22 - 03/01 (1)
- 01/11 - 01/18 (1)
- 11/02 - 11/09 (1)
- 10/26 - 11/02 (2)
- 09/07 - 09/14 (1)
- 08/24 - 08/31 (1)
- 08/10 - 08/17 (3)
- 07/27 - 08/03 (1)
- 07/20 - 07/27 (3)
- 07/06 - 07/13 (5)
- 06/29 - 07/06 (3)
- 06/15 - 06/22 (1)
- 06/01 - 06/08 (2)
- 05/25 - 06/01 (2)
- 05/18 - 05/25 (4)
- 05/11 - 05/18 (2)
- 04/20 - 04/27 (3)
- 04/13 - 04/20 (3)
- 04/06 - 04/13 (1)
- 03/30 - 04/06 (4)
- 03/23 - 03/30 (2)
- 03/16 - 03/23 (2)
- 03/09 - 03/16 (6)
- 02/23 - 03/02 (2)
- 02/16 - 02/23 (4)
- 02/09 - 02/16 (4)
- 02/02 - 02/09 (3)
- 01/26 - 02/02 (1)
- 01/12 - 01/19 (2)
- 01/05 - 01/12 (3)
- 12/29 - 01/05 (1)
- 12/22 - 12/29 (4)
- 12/15 - 12/22 (5)
- 12/01 - 12/08 (3)
- 11/17 - 11/24 (4)
- 11/10 - 11/17 (1)
- 11/03 - 11/10 (3)
- 10/27 - 11/03 (9)
- 10/20 - 10/27 (12)
- 10/13 - 10/20 (2)
- 10/06 - 10/13 (3)
- 09/29 - 10/06 (2)
- 09/01 - 09/08 (4)
- 08/25 - 09/01 (1)
- 08/18 - 08/25 (6)
- 08/11 - 08/18 (4)
- 08/04 - 08/11 (4)
- 07/14 - 07/21 (2)
- 07/07 - 07/14 (5)
- 06/30 - 07/07 (6)
- 06/23 - 06/30 (4)
- 06/16 - 06/23 (1)
- 06/09 - 06/16 (3)
- 06/02 - 06/09 (2)
- 05/19 - 05/26 (4)
- 05/12 - 05/19 (5)
- 04/28 - 05/05 (7)
- 04/21 - 04/28 (1)
- 04/07 - 04/14 (1)
- 03/31 - 04/07 (1)
- 03/24 - 03/31 (4)
- 03/17 - 03/24 (2)
- 03/10 - 03/17 (1)
- 03/03 - 03/10 (4)
- 02/24 - 03/03 (3)
- 02/17 - 02/24 (7)
- 02/10 - 02/17 (1)
- 02/03 - 02/10 (3)
- 01/27 - 02/03 (7)
- 01/13 - 01/20 (1)
- 01/06 - 01/13 (3)
- 12/30 - 01/06 (1)
- 12/23 - 12/30 (6)
- 12/16 - 12/23 (3)
- 12/02 - 12/09 (8)
- 11/25 - 12/02 (7)
- 11/18 - 11/25 (4)
- 11/11 - 11/18 (5)
- 11/04 - 11/11 (7)
- 10/28 - 11/04 (13)
- 10/21 - 10/28 (10)
- 10/14 - 10/21 (7)
- 10/07 - 10/14 (6)
- 09/30 - 10/07 (3)
- 09/23 - 09/30 (9)
- 09/16 - 09/23 (12)
- 09/09 - 09/16 (5)
- 09/02 - 09/09 (16)
- 08/26 - 09/02 (8)
- 08/19 - 08/26 (9)
- 08/12 - 08/19 (11)
- 08/05 - 08/12 (1)
- 07/29 - 08/05 (6)
- 07/22 - 07/29 (4)
- 07/15 - 07/22 (8)
- 07/08 - 07/15 (7)
- 07/01 - 07/08 (7)
- 06/24 - 07/01 (3)
- 06/17 - 06/24 (2)
- 06/10 - 06/17 (5)
- 06/03 - 06/10 (11)
- 05/27 - 06/03 (10)
- 05/20 - 05/27 (9)
- 05/13 - 05/20 (13)
- 05/06 - 05/13 (9)
- 04/29 - 05/06 (5)

